From Chaos to Clarity: My Journey Reimagining Azure RBAC

The Permission Paradox
Picture this: I'm sitting in yet another emergency meeting because someone can't access the resources they need to do their job. The conversation always goes the same way:
"We need to finish this report by end of day," says the finance director.
"I understand," I respond, "but granting full Contributor access to that resource group violates our security policies."
"So what's the solution? We can't miss this deadline."
And there lies the paradox: too restrictive, and productivity suffers; too permissive, and security is compromised. After our quarterly reporting fiasco, I analyzed our access patterns and discovered we were caught in a vicious cycle. IT would implement restrictive permissions following security best practices, users would hit barriers during critical work, we'd implement emergency exceptions, and then during security reviews, we'd tighten everything back up—only to repeat the cycle weeks later.
What made this particularly frustrating was that our Azure environment had grown to over 50 resource groups across multiple subscriptions. Our permission structure had become a complex web of built-in roles, custom roles, and one-off exceptions that nobody fully understood anymore. Audits were nightmares, offboarding employees involved hunting down countless role assignments, and troubleshooting access issues consumed valuable time that could have been spent on strategic initiatives.
We needed a systematic approach that acknowledged a fundamental truth: permissions should follow function, not just organizational structure.
Our Flawed Foundation
Let me be honest – the permission system I inherited was... well, let's just say it was designed with good intentions but poor execution 😬.
Here's what we had:
- Groups based on system access: Database-RO (read-only), Database-RW (read-write)
- Groups based on employment status: Internal-Employees, Ext-Consultants
- Direct role assignments for "special cases" (which somehow became 30% of all users)
This approach was failing spectacularly:
- External consultants often ended up with excessive permissions because no one knew exactly what they needed
- Business users couldn't perform basic tasks without submitting IT tickets
- Every time someone changed departments or roles, their access needed complete reconfiguration
- Admin accounts proliferated because it was the "easy fix" for access problems
The breaking point came when our finance manager called me directly (never a good sign!) because his finance team couldn't upload monthly reports to our storage account. They'd been blocked for three days, and apparently, the deadline for financial reporting was... yesterday. Ouch!
The Revelation: Role-Based Groups
The lightbulb moment came during an all-hands workshop I organized with representatives from each department. Instead of asking "What's your position?" I asked "What do you actually do with our Azure resources?"
The responses were eye-opening. Our finance team wasn't just "finance" – they were report generators, data validators, and compliance reviewers, each requiring different permission sets. Operation needed more than just "read" access – they needed to deploy assets to specific storage containers but never modify infrastructure.
We started mapping functional roles instead of organizational ones:
- Financial Analyst Role: Read access to data lakes and SQL databases, compute capabilities for Power BI, but no infrastructure modification rights
- Operation Manager Role: Contributor access to Operation resource groups, but with custom roles preventing VM or network changes
- Data Engineer Role: Full contributor access to dev environments, but just-in-time privileged access for production
For each role, we created Azure AD security groups with carefully crafted Azure custom roles. The real magic happened when we implemented a matrix model:
[Department Group] + [Functional Role Group] = Actual Permissions
This approach meant someone could move departments without losing functional access, and we could modify department-wide permissions without disrupting functional roles. We implemented Azure PIM (Privileged Identity Management) for sensitive operations, requiring justification and approval for elevated access.
Access should not follow system needs, employment status or arbitrary system groupings
This seems obvious in hindsight, but it was revolutionary for our organization. I sketched out a new naming convention:
- Internal:
[CompanyPrefix]-[Department]-[Role]-[Environment] - External:
[CompanyPrefix]-[Department]-[Role]-[Environment]-EXT
For example:
ACME-Finance-Analyst-PRODACME-Finance-Analyst-PROD-EXT
This hierarchical approach naturally provided least privilege because:
- You only get access appropriate to your department
- Your specific role within that department determines what actions you can perform
- Environments are separated, so having production access doesn't automatically grant development access
- Internal vs. external status is tracked but doesn't fundamentally change your permission set
Mapping to Azure's Built-in Roles
The next revelation came when I dug deeper into Azure's built-in roles. I had known there were a few dozen, but I discovered Azure actually offers 100+ specialized role definitions!
This was the missing piece. Instead of creating custom roles for everything, I could match our organizational roles to Azure's permission sets:
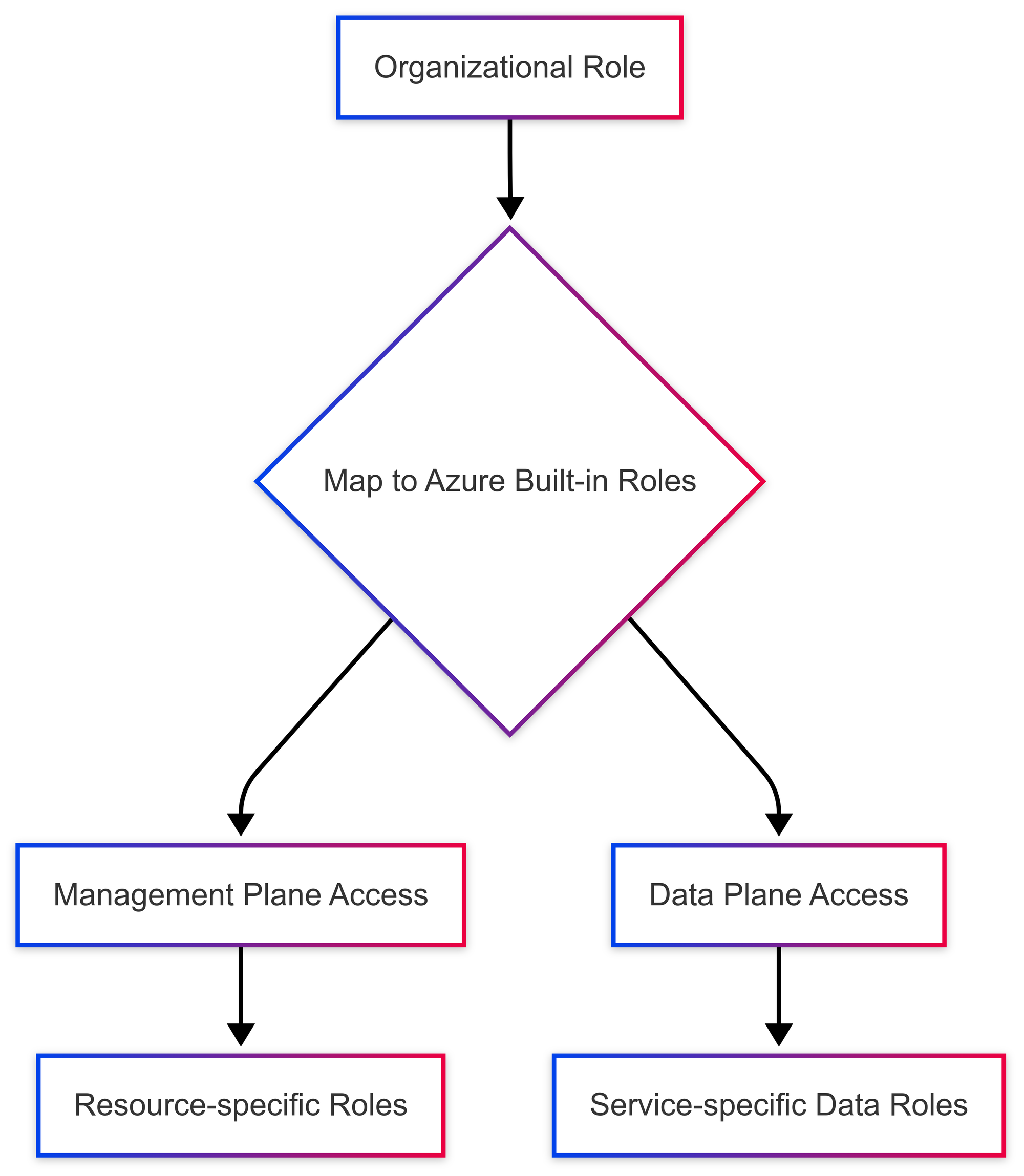
Real examples from our implementation:
- Finance Analysts got
Storage Blob Data Readerfor accessing reports - Finance Reporting specialists received additional
Storage Blob Data Contributorfor uploading reports - Data Engineers received
SQL DB Contributorfor schema management - BI Developers received
Power BI Contributorfor report creation
The efficiency gain was enormous. Instead of maintaining hundreds of custom permission sets, we leveraged Microsoft's well-defined role definitions, saving us maintenance headaches and improving security.
The Data Plane Challenge
Just when I thought I had solved the problem, I realized something critical: "I've only solved half the problem!"
Azure has two distinct permission planes:
- Management Plane: Controls who can create, modify, delete resources (managed via Azure RBAC)
- Data Plane: Controls who can access the data inside those resources (managed via service-specific permissions)
This distinction was crucial. Someone might need to view SQL data but not modify the database itself, or upload blobs but not change storage account settings.
I had to extend our model to handle both planes appropriately:
- Added database role mapping (db_reader, db_writer) for our SQL databases
- Implemented Storage Access Control Lists (ACLs) for more granular folder-level permissions
- Created Key Vault access policies aligned with our role groups
The implementation involved scripts that connected our AD groups to these data plane permissions automatically. For example:
# Example script snippet (simplified)
# This would map our AD groups to database roles
foreach ($group in $departmentRoleGroups) {
if ($group -like "*-DataAnalyst-*") {
Add-DatabaseRoleMember -Database $db -Role "db_datareader" -Member $group
}
if ($group -like "*-DataEngineer-*") {
Add-DatabaseRoleMember -Database $db -Role "db_datareader" -Member $group
Add-DatabaseRoleMember -Database $db -Role "db_datawriter" -Member $group
}
}
Handling Exceptions with Custom Roles
Despite Azure's extensive built-in roles, we still encountered edge cases. Rather than reverting to our old ways, I established a simple rule:
"Exhaust built-in options before creating custom roles."
This approach drastically reduced the potential custom roles from dozens to just a handful. When we did create custom roles, we documented them thoroughly and built them based on the principle of least privilege.
Our custom role process included:
- Clearly defining the business requirement
- Checking if combining existing roles could meet the need
- Creating a custom role with minimum permissions
- Implementing regular review cycles for all custom roles
Results: A New Permission Paradigm
The impact of our new approach was immediately noticeable:
- Access-related incidents decreased by 78% in the first month
- Onboarding time for new employees dropped from days to hours
- Security audit findings related to excessive permissions were reduced to near-zero
- IT tickets for access issues decreased by 65%
Both security and productivity improved simultaneously - a rare win-win in the IT world!
Unexpected benefits emerged too:
- Role transitions became smoother as users simply moved between role groups
- Security reporting became clearer with our standardized naming
- Our cloud governance team could easily understand who had what access and why
The feedback from across the organization was overwhelmingly positive. Even our consultants appreciated knowing exactly what they had access to and why.
Lessons for Your Journey
If you're facing similar RBAC challenges, here are my key principles for success:
- Align with organizational structure, not technical systems
- Use a consistent, meaningful naming convention
- Leverage Azure's built-in roles whenever possible
- Remember both management plane and data plane access
- Document everything, especially exceptions
Common pitfalls to avoid:
- Don't grant admin access as a quick fix
- Don't create one-off groups for individuals
- Don't forget to remove temporary access
- Don't neglect regular access reviews
To get started, take these simple first steps:
- Inventory your current AD groups and role assignments
- Map your organizational chart to identify true roles
- Start with one department as a pilot for the new approach
- Build automation to maintain consistency
The Journey Never Ends - Your Turn to Tackle RBAC!
We've come a long way from that emergency meeting with the finance director! From a chaotic permissions nightmare to a structured, role-based approach that aligns with our business. But here's the truth - RBAC is never "done." It evolves as your organization and Azure itself changes.
Key Takeaways:
- Start with organizational roles, not technical permissions
- Leverage Azure's built-in capabilities before creating custom solutions
- Remember both management plane and data plane access
- Automate and document everything
Share Your Story:
I'd love to hear about your RBAC challenges and victories! What permission management headaches keep you up at night? Drop a comment below or connect with me - let's learn from each other's experiences.
After all, the best security models don't just protect data - they enable people to do their best work. 🔐
